Dieser Blogbeitrag ist nur in englischer Sprache verfügbar. | This blog post is only available in English.
This is part II of our blog series: “Road to the AWS Security Specialty”
You can find part I here: Road to the AWS Security Specialty – Part I: How to prepare for the AWS Security Specialty
In this blogpost I want to give you a more technical view into my take-aways from the security specialty and why they are so helpful during day-to-day business with AWS. Through this you will hopefully also get a better idea of the general content of the certification.
Security Basics
Knowing all the basics from IAM, S3 and Security Policies in and out helps you so much in every project.
Generally, there are several topics to consider in AWS.
Visibility – You should always have a good overview over all your resources and status.
Auditability – Do all resources comply with policies + regulations?
Controllability – Is my data controlled? Do I need Dedicated hardware?
Agility – How quickly can you adapt to changes?
Automation – Are all possible processes automated?
Scale – The scale of AWS is on your side.
Example problems which might come up:
What happens when you have conflicting policies?
Short answer: an explicit deny always overrides an allow.
For example: Your IAM policy allows s3 Bucket access, but the bucket denies the access, then the request will still be denied.
How do I force encryption using S3?
You can deny all actions in your bucket which aren’t using encryption through your bucket policy using the aws:secureTransport phrase.
Best practices for KMS
KMS is a managed service from AWS, which makes it easy to create and control encryption keys used to encrypt data.
In my projects KMS is often used for a lot of different services.
KMS uses a Customer Master Key which consists of an alias, the creation date, a description, the key state and the key material.
There are different options for your Customer Master Key, for most use-cases especially the rotation of keys is super important. In the following table the three options and differences are shown.
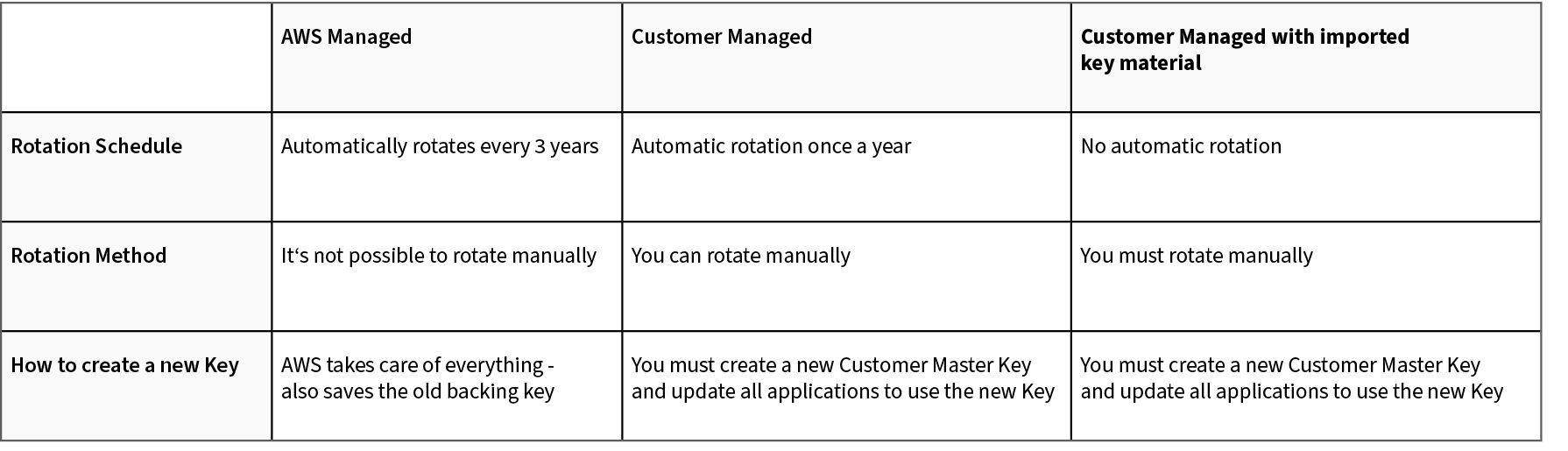
One trouble people often have with KMS is, that they forget that you must give the user access to the KMS key as well. If the contents in your S3 bucket are encrypted only giving access to S3 won’t be enough, you’ll also have to give the user permission to use KMS to decrypt data.
VPC
Knowing to properly secure and monitor your VPC and its traffic is one of the most important tasks in your cloud infrastructure.
Regarding Security Groups and Network Access Control Lists you should know the differences:
Security Groups are Stateful – Response Traffic is allowed inbound regardless of inbound rules
Network Access Control Lists are Stateless – A rule is required to allow response traffic to inbound requests
VPC Flow Logs enable you to capture information about the IP traffic going to and from network interfaces and should always be activated.
There are three different types of Load Balancers. The Application Load Balancer for HTTP and HTTPS traffic, the Network Load Balancer for TCP traffic and the Classic Load Balancer which you will only use if you have an application running in the EC2-Classic network. The Application Load Balancer is used 9 out of 10 cases unless you need ultra-high performance or a static IP address.
Load Balancer and TLS/SSL Termination
When using a LB you can either terminate TLS/SSL on the LB or an EC2 instance.
When it’s terminated on the LB, the LB decrypts the encrypted request and sends it to the application as plain text over the local private network in the VPC. This offloads processing from your EC2 instance to the LB but also raises several security concerns. The traffic between Load Balancer and instance is unencrypted. If the compliance rule is to use encryption end-to-end all the way, the requests always must be terminated on the EC2 instances.
Regarding access to your instances or applications, the AWS Session Manager is usually the easiest, safest and recommended way for that. It is also cheaper than hosting a bastion host for that purpose.
DDOS Resiliency
AWS WAF – Web Application Firewall offers protections against DDoS attacks but only if you use CloudFront or an Application Load Balancer. Besides that, the steps to prepare are:
Minimize the attack surface – use a bastion host
- Be ready to scale to absorb the attack
- Safeguard exposed resources
- Use CloudFront for geo restriction / blocking
- Use Route 53 to redirect traffic
- Learn the normal behavior of your applications
- Create a plan for attacks
Real world problems
What to do when an EC2 has been compromised?
- Stop instance immediately
- Take a snapshot of the EBS volume
- Deploy instance into an isolated environment -> no internet access
- Access the instance using a forensic workstation
- Read through the logs
What to do when access keys were leaked?
- Disable access keys
- Create new keys
- Delete old ones
What to do when API Gateway get overwhelmed?
- To prevent your API from being overwhelmed by too many requests, AWS throttles requests
- When requests exceed steady-state request rate and burst limits
- API Gateway fails the limit-exceeding requests and returns 429 too many requests error
- Default 10.000 requests per seconds steady-state
- Burst is 5000 requests across all APIs within an AWS account
- Limits can be increased
Secretsmanager vs Parameter Store
When storing secrets in AWS – Secrets Manager and the Parameter Store are usually the options you have to consider.
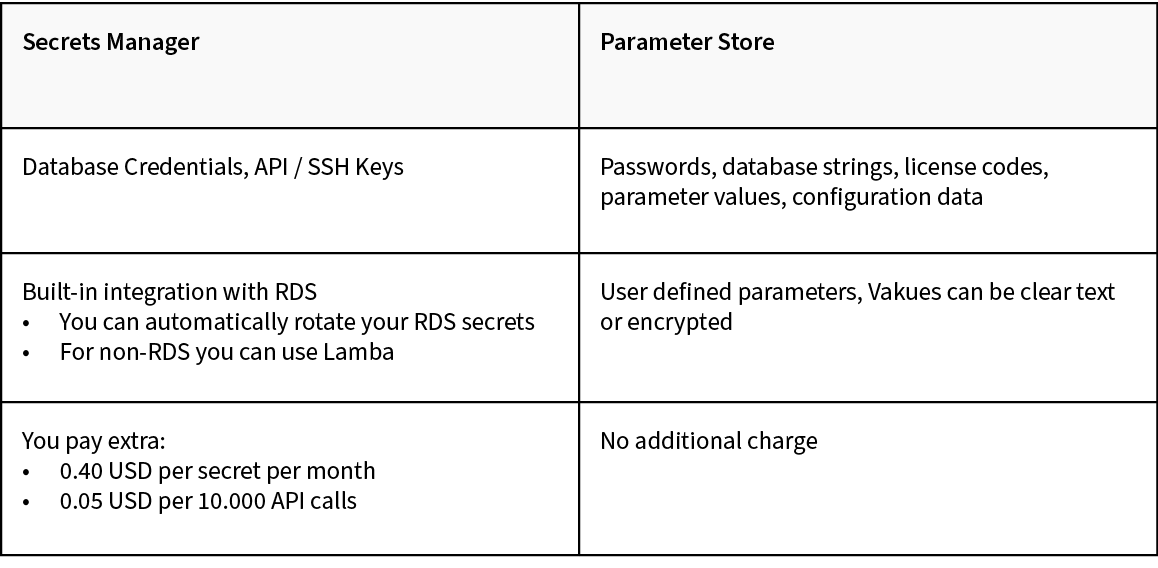
In short: if you have database credentials or API/SSH keys use Secrets Manager for everything else use the Parameter Store.
I hope I could give a more detailed view into the topics the security specialty touches. I really enjoyed learning about all of them especially because during the preparation I’d always think of ways I could use my knowledge in the future. I had several situations where the information already helped me. One time a coworker had a problem where he couldn’t open a file in S3. I investigated it and instantly saw that the contents were encrypted via KMS. I asked him if he had permissions to decrypt via KMS – he didn’t. He got the permissions and was able to view the file.
If you use AWS on the daily, I definitely recommend taking the AWS Security Specialty.
Happy learning!
This is part II of our blog series: “Road to the AWS Security Specialty”
You can find part I here: Road to the AWS Security Specialty – Part I: How to prepare for the AWS Security Specialty






0 Kommentare